DNS amplification attack is mainly DDoS (distributed denial-of-service) attack. Mainly attacker target DNS server and send huge amount of traffic on DNS server.
Every system has limitation, so if you send huge amount of request on the system server can be crashed. At this situation attacker take advantage and they are crashed or down your service. You actual user suffer and boom.
To launch a DNS amplification attack, attackers use maliciously crafted Domain Name System (DNS) messages that are sent from vulnerable or misconfigured servers to generate enormous amounts of traffic. The benefits associated with this type of attack include increased anonymity since the source IP address can be spoofed, and relatively low costs for execution compared to other DDoS attacks.
On a global scale, 88% of organizations have suffered DNS attacks — with companies encountering an average of seven attacks per year at a cost of $942 thousand per attack, according to the IDC 2022 Global DNS Threat Report. In addition to financial losses, other serious consequences of DNS attacks include data theft, reputation damage, website downtime and malware infections.
DNS Amplification Attack Work
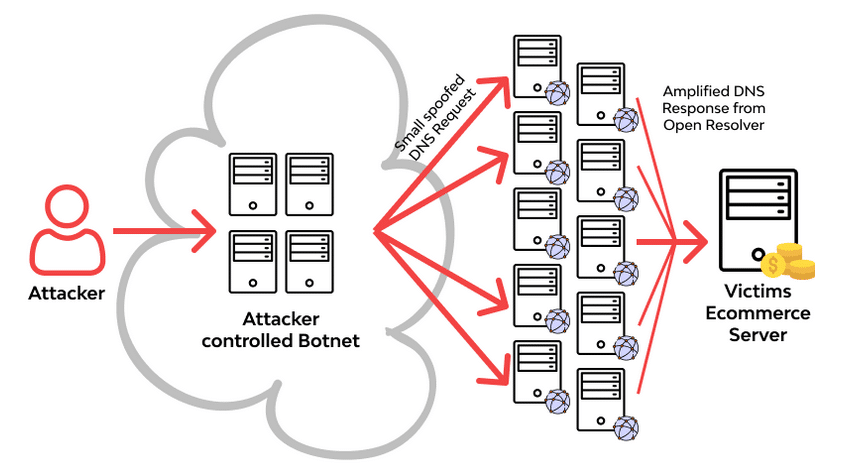
Hide the Source IP Address:
The attacker typically hide the source IP address to make it appear as if the requests are coming from a legitimate source.
Sending DNS Queries:
The attacker sends a large number of DNS queries to open DNS resolvers on the internet. These resolvers are configured to respond to DNS queries from any source. Victim DNS server is the target and send the request until DNS server burn out.
Amplification Factor:
The attacker crafts the DNS queries in such a way that the response generated by the DNS server is much larger than the original query. This is known as the amplification factor.
Target IP Address:
The target IP address (victim) is flooded with these amplified DNS responses, overwhelming its network and server resources.
Denial of Service:
Due to the sheer volume of traffic generated by the amplification attack, the target’s network and servers become congested, leading to a denial of service for legitimate users.
Reflection:
The attack often involves reflection, where the attacker utilizes third-party systems (DNS resolvers) to amplify and reflect the attack traffic toward the target. This makes it difficult to trace the attack back to its origin.
Botnet Usage:
In many cases, attackers use botnets (networks of compromised computers) to carry out these attacks, making it harder to trace the source of the attack and increasing the scale of the assault.
How to mitigate the DNS amplification attack.
DNS Rate Limiting:
- Configuring DNS servers to limit the number of queries they will respond to from a single source within a specific time frame.
Source IP Validation:
- Implementing measures to validate the source IP address of DNS queries to prevent IP address spoofing.
Firewall Rules:
- Configuring firewalls to block traffic from known malicious sources or to limit the rate of incoming DNS traffic.
DDoS Mitigation Services:
- Employing DDoS mitigation services and appliances that can identify and filter out malicious traffic before it reaches the target network.
DNS Header Format
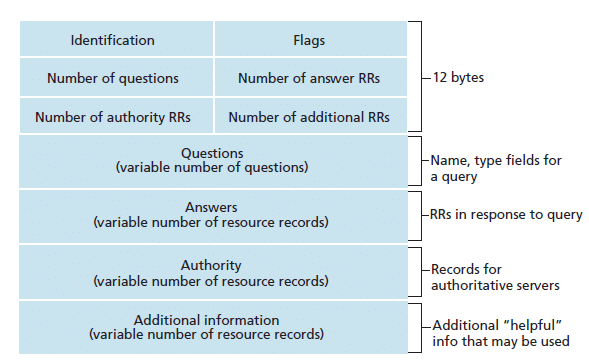
Here’s a breakdown of the DNS header fields:
- Identification (ID) (16 bits):
- A 16-bit identifier assigned by the program that generates the DNS request. This identifier is copied into the corresponding reply and is used to match responses with the queries.
- Flags (16 bits):
- The Flags field contains several subfields, including:
- QR (1 bit): Query/Response flag. 0 indicates a query, and 1 indicates a response.
- Opcode (4 bits): Indicates the kind of query being made (standard query, inverse query, server status request, etc.).
- AA (1 bit): Authoritative Answer. Set to 1 if the responding server is authoritative for the domain in question.
- TC (1 bit): Truncation flag. Set to 1 if the message was truncated due to its length.
- RD (1 bit): Recursion Desired. Set to 1 if the client requests recursion from the server.
- RA (1 bit): Recursion Available. Set to 1 if the server supports recursion.
- Z (3 bits): Reserved for future use.
- RCODE (4 bits): Response code. Indicates the status of the response (e.g., success, name error, format error).
- The Flags field contains several subfields, including:
- Question Count (QDCOUNT) (16 bits):
- An unsigned 16-bit integer specifying the number of entries in the question section.
- Answer Record Count (ANCOUNT) (16 bits):
- An unsigned 16-bit integer specifying the number of resource records in the answer section.
- Authority Record Count (NSCOUNT) (16 bits):
- An unsigned 16-bit integer specifying the number of resource records in the authority section.
- Additional Record Count (ARCOUNT) (16 bits):
- An unsigned 16-bit integer specifying the number of resource records in the additional section.
Each DNS packet contains a header followed by a variable number of question, answer, authority, and additional resource record sections, depending on the type of DNS message (query or response) and the specific details of the transaction.
So DNS is UDP packet, it can be TCP packet but most of the organization prefer to use UDP. Science DNS is UDP so the packet is controlling so hard that’s why attacker can easily exploits DNS
