Cybersecurity for Digital Marketers: Helpful for all internet user!
If you’re deeply involved with digital marketing – whether you’re part of an agency, working independently, or in-house – chances are you’ve encountered a security issue at some point. These concerns, varying in threat levels, are extremely prevalent and can pose significant risks, potentially causing extensive damage to a site and impacting its long-term organic performance.
Digital marketer create asset in online and they get revenue from there. So always hacker or attacker target their asset and blackmailing the marketer. How attacker hack website or social media platform. It’s mainly do by Phishing Attack.
Phishing attack is simple and easy to hack any website or social media platform.
What is Phishing Attack?
Phishing is a type of cyber attack in which attackers use deceptive emails, messages, or websites to trick individuals into providing sensitive information, such as usernames, passwords, credit card details, or other personal information.

The goal of a phishing attack is to exploit human psychology and manipulate individuals into taking actions that compromise their security.
How Attacker make Phishing Attack.
Digital marketers can be targeted by hackers or attackers through various methods, as they often handle valuable data, run online campaigns, and have access to multiple online platforms. Here are some common ways hackers may target digital marketers:
Phishing Attacks: Sometimes attacker give you his identity as a sponsor or client. And he wan to give you service. He share link for work details, you click their and you are attacked. So be careful.
Email Phishing: Hackers may send deceptive emails pretending to be from trusted sources or business partners. These emails may contain malicious links or attachments aiming to capture login credentials or install malware.
Cybersecurity for Digital Marketers is very important to careful about email because 80 of attack with phishing mail attack. So be careful Digital Marketers before open any mail.
Spear Phishing: Attackers may personalize their phishing attempts, tailoring messages specifically for digital marketers based on their roles, responsibilities, or industry contacts.
Social Engineering:
Impersonation: Attackers may create fake social media profiles or email accounts, pretending to be colleagues, clients, or executives to gain trust and extract sensitive information.

Manipulation: Hackers might exploit personal information shared on social media platforms to craft convincing messages or gain unauthorized access to accounts.
Credential Attacks:
Brute Force Attacks: Attempting to gain access to digital marketing accounts by systematically trying different username and password combinations.
Credential Stuffing: Using previously leaked username and password combinations to gain unauthorized access to accounts where individuals have reused passwords.
Malware and Ransomware:
Malicious Downloads: Hackers may use malware-laden attachments or links in emails or messages to infect a digital marketer’s computer with malware.
Ransomware Attacks: Digital marketers may be targeted with ransomware, where their files or systems are encrypted, and the attacker demands payment for their release.

Supply Chain Attacks:
Compromising Third-Party Tools: Attackers may target the tools and platforms commonly used by digital marketers. If marketers use compromised tools, the attackers can gain unauthorized access to sensitive data.
Unsecured Wi-Fi Networks:

Man-in-the-Middle Attacks: If digital marketers connect to unsecured Wi-Fi networks, attackers may intercept and manipulate their communication, potentially gaining access to login credentials or sensitive information.
Note: Cybersecurity for Digital Marketers always use your private wifi. Don’t use public wifi because it’s very harmful for you.
To mitigate these risks, digital marketers should prioritize cybersecurity measures, including:
- Regularly updating and patching software.
- Implementing strong, unique passwords and enabling two-factor authentication.
- Educating themselves and their teams about cybersecurity best practices.
- Being cautious with emails, especially those with unexpected links or attachments.
- Verifying the legitimacy of communication from colleagues or clients, especially if it involves sensitive information.
- Using secure and trusted networks when accessing work-related accounts and platforms.
How your website protect form cyber attack?
As a digital marker your website is very important for you. Because it’s only your earning source.
Website Integrity:
A secure website is fundamental to maintaining its integrity. If a website is compromised, it can lead to unauthorized access, defacement, or injection of malicious content. Such incidents can harm the website’s reputation and result in a loss of trust from both users and search engines.
User Trust and Confidence:
Users are more likely to engage with websites that they trust. If a website is known to have security issues, visitors may be hesitant to interact with it, leading to increased bounce rates and decreased dwell time. These factors can negatively impact SEO rankings. [Cybersecurity for Digital Marketers]
Data Protection and Privacy Compliance:
Data protection and privacy compliance are increasingly integral to the field of SEO (Search Engine Optimization). As search engines prioritize user experience and privacy, adhering to data protection regulations becomes crucial for maintaining SEO best practices.

Here’s how data protection and privacy compliance intersect with SEO:
- User Trust and Retention:
- Prioritizing data protection instills trust in users. When visitors feel confident that their personal information is handled responsibly, they are more likely to engage with a website, stay longer, and return. Positive user behavior contributes to better SEO rankings.
- Search Engine Algorithms:
- Search engines like Google consider user experience as a ranking factor. Websites that prioritize data protection and privacy align with search engines’ goals of providing a safe and secure online environment. Compliance with regulations such as GDPR and CCPA contributes positively to algorithmic considerations.
- Legal Compliance Signals:
- Search engines are increasingly likely to favor websites that comply with data protection laws. Compliance can be seen as a positive signal in the eyes of search algorithms, potentially influencing rankings.
- Content Personalization:
- With privacy regulations emphasizing user consent for data processing, websites need to be transparent about how they collect and use data. This transparency ensures that SEO strategies, such as content personalization, are aligned with privacy regulations.
- Cookie Policies and Consent:
- Websites often use cookies for tracking and analytics. Ensuring compliance with regulations requires transparent cookie policies and obtaining user consent. Failing to do so can lead to legal issues and negatively impact SEO.
- Mobile Responsiveness and Privacy:
- Mobile-friendliness is a significant SEO factor. As mobile devices handle vast amounts of personal data, mobile websites must prioritize data protection. Compliance with mobile privacy standards is crucial for maintaining SEO rankings.
- Local SEO Considerations:
- Local SEO efforts can be impacted by data protection regulations specific to regions. Understanding and adhering to local privacy laws contribute to a comprehensive SEO strategy.
- Security and Site Performance:
- Secure websites with robust data protection measures tend to perform better in terms of speed and overall performance. This is critical for SEO, as site speed is a known ranking factor.
- Avoidance of Penalties:
- Non-compliance with data protection laws can result in legal penalties. In extreme cases, search engines may penalize websites for violating privacy regulations, leading to a negative impact on SEO rankings.
- Ethical SEO Practices:
- Aligning with data protection and privacy standards is not just a legal requirement but also an ethical consideration. Adhering to ethical SEO practices contributes to a positive online reputation, enhancing the overall trustworthiness of a website.
- Optimized Forms and User Engagement:
- Websites collecting user data through forms must ensure compliance with privacy regulations. Optimizing forms for user experience and clearly communicating data handling practices contribute to positive SEO signals.
Data protection and privacy compliance are integral components of a holistic SEO strategy. Prioritizing user privacy not only ensures legal adherence but also aligns with the evolving expectations of search engines and users.
It contributes to positive SEO signals, enhances user trust, and mitigates the risk of legal penalties or reputational damage. As privacy regulations continue to evolve, staying informed and proactive in compliance efforts is crucial for sustaining SEO success.
SEO Penalties and Rankings:
Search engines actively penalize websites with security vulnerabilities. If a website is compromised and poses a threat to users, search engines may lower its rankings or remove it from search results altogether. Regular security audits and prompt resolution of vulnerabilities are essential to maintain SEO rankings.
Cybersecurity for Digital Marketers: Black Hat SEO Techniques:
Hackers may exploit vulnerabilities in a website to deploy black hat SEO techniques, such as injecting spammy links or cloaking content.

Search engines are quick to penalize websites engaging in such activities. Cybersecurity measures help prevent unauthorized access and manipulation of a website’s content.
Site Speed and Performance:

Security measures can also contribute to a website’s overall performance. Malicious activities, such as DDoS attacks, can degrade a site’s speed and availability. Search engines consider site speed as a ranking factor, and a secure website is better equipped to handle such attacks, ensuring optimal performance.
Enhanced Crawlability:
A secure website is more likely to be efficiently crawled and indexed by search engine bots. Security issues, such as server downtime due to attacks, can hinder the crawling process and impact how search engines index and rank the content.
Protecting Online Reputation:
Cybersecurity helps in safeguarding the online reputation of a brand or business. A compromised website can be used to spread malicious content or defame a brand, leading to long-term damage. Maintaining a secure online presence contributes to a positive reputation, which is crucial for SEO.

Cybersecurity is an integral part of SEO because it not only protects the website and user data but also ensures that the website meets the criteria set by search engines for rankings. By prioritizing cybersecurity, digital marketers can maintain a strong online presence, build user trust, and enhance their website’s performance in search engine results
Website build platform
In the world of cybersecurity, attackers typically kick off their reconnaissance efforts by identifying the software running on a target site. Keeping popular software up-to-date is crucial because developers regularly release patches to address new vulnerabilities. If your site happens to be running an outdated version of a particular platform, it becomes an easier target for compromise.
Discovering this information is often considered the low-hanging fruit for attackers. Various methods can be employed, and online tools like BuiltWith or WhatWeb serve as effective means to unveil the software and its version powering a specific domain.
Once armed with this knowledge, the next step is to determine the most recent version of the software package. If your site is already using the latest version, that’s great news.
However, if it turns out you’re running an outdated version, it’s a prudent move to investigate whether there have been any significant vulnerabilities patched between your current version and the latest release.
Keeping software updated not only ensures optimal performance but also plays a critical role in fortifying your digital defenses against potential security threats.
WordPress Website Hacking Things
Being the most widely utilized CMS online, WordPress is a constant target for attackers. It’s crucial to understand how to conduct fundamental security checks on websites relying on this platform and to be able to counsel clients on general best practices for WordPress security. Failing to do so can expose their site – and their SEO – to long-term vulnerabilities.
The majority of basic WordPress attacks stem from weak login security. If you’re employing standard usernames or still have your administrator username set as ‘admin,’ you’re taking on unnecessary risks.
Changing your site’s login URL is also advisable. The default URL (‘wp-login.php’) is the go-to for automatic vulnerability scanners.
To initiate a robust approach to WordPress security, consider using a security plugin that, when regularly updated, aids in monitoring and safeguarding your site. These tools come equipped with various features designed to enhance your site’s security. Ensure your website has, at the very least, the basic features enabled by going through the settings.
Well-known examples include All in One and Sucuri Security, both of which actively monitor and scan for potential hacking events. They also feature firewall capabilities that permanently block suspicious visitors.
In essence, it’s imperative to assess, research, and update each plugin and script in use. Investing time in keeping your plugins updated is a far better option than leaving yourself susceptible to easy targeting.
Cybersecurity for Digital Marketers is important to use updated them and plugin.
Login Folder on WordPress
Even if your site doesn’t rely on WordPress, that doesn’t mean it won’t be targeted. A custom or proprietary platform can still fall victim to an attack if you’re not following basic security protocols.

For example, it’s fairly simple for someone to find your website’s login URL, which serves as the perfect target for any attacker.
Many websites overtly block the back-end login folder in their robots.txt file. This might look something like the following:
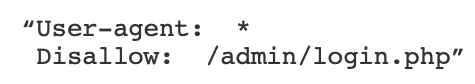
Given this is a publicly available file, this amounts to broadcasting your login URL to anyone looking to force their way into your website.
Even if you’ve got this covered, another simple Google search can often provide a hacker with this information: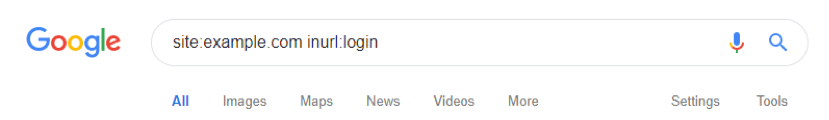
A ‘site:’ search for URLs with ‘login’ or ‘admin’ in them can easily turn up a login page that’s been indexed. Ensure your robots.txt doesn’t give this away and use ‘noindex’ meta tags on your login pages to prevent them being accidentally indexed.
Share Hosting is ideal for Hacker
Many small websites operate on shared hosting servers. In such instances, the security of your site is essentially only as robust as the least secure website on that server.
If an attacker successfully breaches one site, there’s an increased likelihood of gaining access to the entire server and all the sites hosted on it.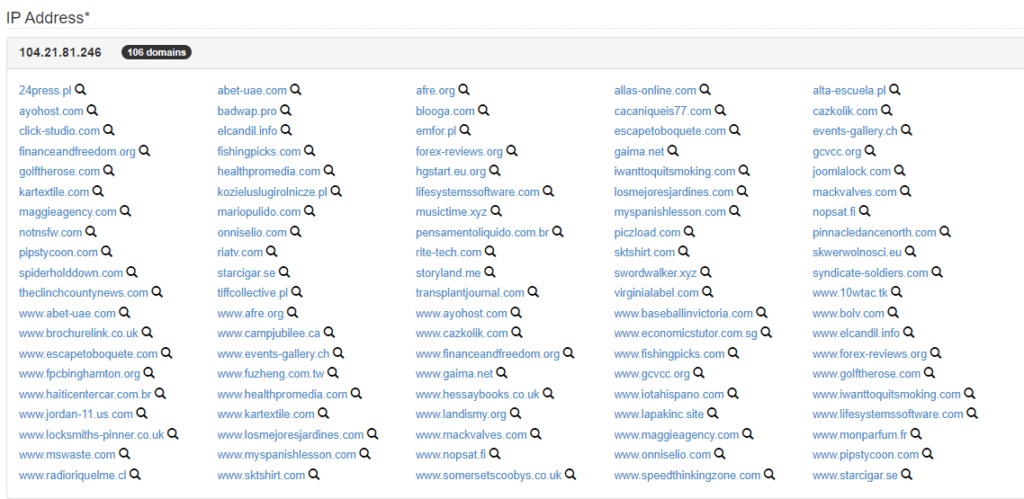
To check whether a specific site is on a shared server, you can use straightforward tools like SpyOnWeb. By entering the website’s domain, you’ll receive a swift overview of all other domains associated with the same IP address.
If these domains don’t share the same owner, it indicates that the website is indeed part of a shared hosting server. This information is valuable for assessing the potential security risks associated with the hosting environment of a particular website.
SSL update on your website
SSL (Secure Sockets Layer) updates are crucial for ensuring a secure website, even though having HTTPS is important. It’s essential to recognize that not all SSL certificates offer the same level of security.
Over the past few years, there have been concerns regarding vulnerabilities in SSL, with notable incidents like the DROWN and Heartbleed attacks.
As a general rule, it’s advisable to invest in a high-grade SSL certificate that is fully up-to-date and has no known susceptibilities. To assess the quality of a certificate on a specific site, you can utilize tools like SSL Labs.
Regularly testing your SSL certificate is a wise practice to align with the latest security standards. With the ever-evolving nature of cybersecurity threats, staying proactive and ensuring your SSL certificate is free from vulnerabilities is essential for maintaining a robust security posture.
Cybersecurity for Digital Marketers use ssl certificate to protect your website confidential data.
